1.0 R-WlanXDecrypter
Here I present a utility that I created for the generation of dictionaries default key of R, a company of Galicia. Are known as R-wlanX (where X is a number) or similar names. Recently many wifimedia_R-XXXX networks are also seen (the X are numbers), which also analyze.
I have seen that there is a Rwlandecrypter aí (why I put another name), but I've tried and has not convinced me, creates a dictionary of only 14 MB which includes only a small part of the possible keys by default.
Before presenting the program I would like to analyze these networks to be clear what kind of passwords used routers R by default.
Analysis
Networks wifimedia_R-XXXX:
These networks are those that come with certain routers that provides R. The company provides them if you have hired a service called wifimedia. This service comes standard connections so gratiuta to 30Mb or more, but can also be hired for a price for less speed connections, but this is not the last common. That is, these networks are often high speed. Bring WPA / WPA2, however, the default password is ridiculous. For this reason sometimes the technician who installed the router change this password, but that's not normal.
The default password for these networks is the router's MAC finished with the last digit 0, lowercase letters are often but sometimes can be capitalized. An example:
As can be seen the safety of these routers is ridiculous, needless or capture packets or use the R-WlanXDecrypter program or anything.
R-wlanX networks with WEP:
The first is to clarify that neither the SSID or MAC provides details on the key. Normally the number of SSID channel usually (but not always) the AP. Not always the exact format of "R-wlanX" is true, sometimes mixed uppercase lowercase, no spaces sometimes, sometimes scripts, sometimes nothing separating the words; and sometimes additional words are in the SSID.
The most universal way to define default passwords R is being followed zeros numbers. How many numbers before the 0's? Typically 8, on occasion independent 6. Now we have four possibilities this type of default passwords (passwords ruling over 128 bits):
Do they mean something numbers? this topic is quite mysterious:
-Some Key start for one year (ex .: "2008") followed by four random numbers; is believed that the year is manufacturing router, but we found many future years (ex .: "2023"), so do not seem to be the case. Also most begin with 2 keys, if we reduce the search range can start looking for clues that start with 2. It was recently discovered that this number seems to be the ID that R assigned to your client (completely unknown thing for us that only is present in their bills).
-In Other cases, especially when treated 6 numbers followed by 0's (instead of 8) is believed to be the phone number without the prefix. Knowing this does not help us much but if these keys are only 6 numbers followed by 0's instead of 8, which reduces very sustencialmente our interval search
Well, whatever the origin of these numbers, we find that only vary at most 8 digits, which are always numbers, so we have 10 ^ 8 = 100,000,000 possibilities for each type of passwords, which are also not many. In an actual laptop midrange all the keys would be checked in 2 hours or less so.
R-wlanX networks with WPA keys:
Today it is more common to see routers with default keys R WPA with WEP keys, although the pattern is similar to WEP passwords. In this case the default passwords are key 8 digits but without following the 0's, the XXXXXXXX (ex .: "20109456") style. This number seems to be the ID of the client, and it seems that this number also starts in most cases (so far in all tested) for 2, so that passwords are we would reduce only those that begin with 2 (Style 2XXXXXXX).
Also there have been cases WPA key 10 digits, although still only 8 variables digits, but with two 0's below (although these are much less common). XXXXXXXX00 style (ex .: "2010945600"). As with the keys to 8 digits only found cases of passwords that began 2 to 2XXXXXXX00 style.
The third pattern WPA key is detected is a 16 digit password, but it really is a password of 8 variables digits repeated twice, at ABCDEFGHABCDEFGH style (ex .: "2015483920154839").
A modest rate of cracking of 1000key / sec, it would take about 28horas to check the complete dictionary of keys. If we test only the keys that begin with 2, it would take about 3 hours to check.
This concludes the analysis and proceed to explain the application.
R-WlanXDecrypter
The program currently supports Unix and Windows platforms. The basic options are needed to create dictionaries for WEP passwords, and additional options, which I will explain later, are a way to create custom dictionaries, and also serve for WPA keys.
The project is now available with source code on GitHub. One tag for each version release will be created, and major developments are made on the master:
https://github.com/millanzarreta/R-WlanXDecrypter
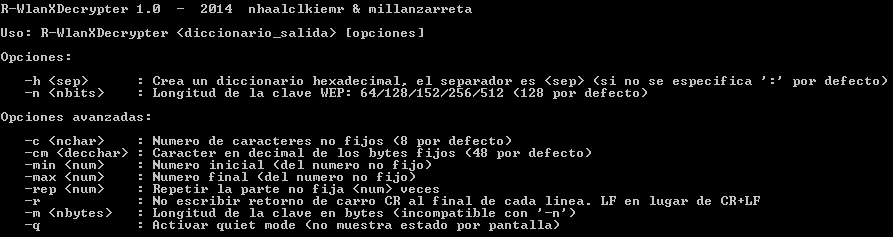
Basic Options
Using only these options can create universal dictionaries for R passwords with WEP keys. If creais dictionary for aircrack-ng is important to remember that supports dictionaries larger than 2GB. By default, the program creates keys 8 digits followed by 0's (and thus also include the 6-digit). The notes of the new version of aircrack-ng comment that dictionaries should support larger than 2GB, but empirically checking it to me still not working.
'First we will create a dictionary for passwords ASCII 128bit, will occupy 1,40GB:
Now we will create a dictionary for passwords Hexadecimal 64-bit, take 1,48GB:
With these two dictionaries should suffice for most routers R. Even so can always generate a password dictionary to Hexadecimal 128bit. This dictionary occupy 3,72GB:
If we create the dictionary for aircrack-ng remember dictionaries that does not support more than 2GB, so we have to split into two this dictionary (for example, two dictionaries of 1,86GB each):
-Also Can create a dictionary for 64-bit ASCII key, but never see any of this in R dictionary occupies only 683KB:
With the default options dictionaries generated are of great size and with many words, and can take a long time depending on the equipment check them all. With these advanced options can be defined more custom dictionaries. Several useful examples:
As we said, sometimes the keys are only 6 numbers followed by 0's, then create the above dictionaries (except 64bit ASCII because it makes no sense to reduce it) but for 6 bytes variables instead of 8. The dictionaries created 67,7MB occupy only 3 together. In this way we can do a quick check with the aircrack-ng for key numbers with 6 variables before using large dictionaries:
[/ List]
-and Named many of the default passwords of R typically start -min and -max 2. Using dictionaries can define only that range (starting with 2). The 3 dictionaries that are creating (128bit ascii, hex 64bit and 128bit hex) occupy the tenth of each:
Case WPA:
We can use the program with options to create a dictionary views for key WPA. In this case we have to indicate that you create a dictionary of 8 digits, all variables. The dictionary will 100,000,000 keys and take 953.67MB:
If we want to reduce the search time, we can create a dictionary that contains only the keys starting with 2. The dictionary has 10,000,000 and occupies 95.37MB keys:
Most of R WPA keys are 8 figures, but also have detected some cases key 10 digit numbers with 8 variables followed by two 0's. To create the dictionary would be as follows:
-The Complete dictionary for WPA 10 has 100,000,000 key figures and occupies 1144.41MB:
If you only want to reduce the search time, we can test the keys starting with 2. This dictionary has 10,000,000 and occupies 114.44MB key.
Finally, it has also detected a pattern of 16-digit passwords that are actually passwords 8 variables digits that repeat.
-The Complete dictionary for WPA 16 has 100,000,000 key figures and occupies 1716.61MB:
If you only want to reduce the search time, we can test the keys starting with 2. This dictionary has 10,000,000 and occupies 171.77MB key.
So far all the networks analyzed starting with the number 2. Therefore it is recommended to start with dictionaries that only recojen keys starting with 2 and use the general dictionaries of 8 and 10 figures only in the event that they do not work.
Discharge
Includes compiled versions for linux and windows and source code.
Current-version (1.0):
-mirror 1: https://www.dropbox.com/s/5aojiwb58nqqvkm/R-WlanXDecrypter1.0.zip?dl=1
-mirror 2: https://github.com/millanzarreta/R-WlanXDecrypter/raw/release-1.0/R-WlanXDecrypter1.0.zip
Old-versions (0.9):
-mirror 1: https://www.dropbox.com/s/srlrovcubxm3son/R-WlanXDecrypter0.9.zip?dl=1
-mirror 2: https://github.com/millanzarreta/R-WlanXDecrypter/raw/release-0.9/R-WlanXDecrypter0.9.zip
Old-versions (0.8):
-mirror 1: https://www.dropbox.com/s/p0mt5t0uyjmqdxt/R-WlanXDecrypter0.8.rar?dl=1
-mirror 2: https://github.com/millanzarreta/R-WlanXDecrypter/raw/release-0.8/R-WlanXDecrypter0.8.rar
Changelog
v1.0 [27/10/2014]
-----------------
+ Added option -Rep <num> which allows the variable portion repeat <num> times
+ Change in type of variables with more acceptable
+ Fixed error showing the process of creating bad if the dictionary was larger than 2GB
+ Fixed a bug that was produced at times to create hexadecimal dictionaries and that produced a word size than the specified
+ Fix several minor bugs
v0.9 [11/10/2010]
-----------------
+ Show final file size and number of keys
Show status process +
+ Added -q quiet mode
+ Fixed bug in -min and -max options
+ Small loop optimization key generator
+ Correction of small general failures
v0.8 [06/10/2010]
-----------------
+ First public release
Appendix: Using dictionaries Hexadecimal in aircrack-ng
To define aircrack-ng one hexadeximal dictionary must specify h: before the path of the dictionary and we must always specify the length of the WEP keys in the dictionary are using:
It seems that the new version of aircrack-ng these bugs still present.
Here I present a utility that I created for the generation of dictionaries default key of R, a company of Galicia. Are known as R-wlanX (where X is a number) or similar names. Recently many wifimedia_R-XXXX networks are also seen (the X are numbers), which also analyze.
I have seen that there is a Rwlandecrypter aí (why I put another name), but I've tried and has not convinced me, creates a dictionary of only 14 MB which includes only a small part of the possible keys by default.
Before presenting the program I would like to analyze these networks to be clear what kind of passwords used routers R by default.
Analysis
Networks wifimedia_R-XXXX:
These networks are those that come with certain routers that provides R. The company provides them if you have hired a service called wifimedia. This service comes standard connections so gratiuta to 30Mb or more, but can also be hired for a price for less speed connections, but this is not the last common. That is, these networks are often high speed. Bring WPA / WPA2, however, the default password is ridiculous. For this reason sometimes the technician who installed the router change this password, but that's not normal.
The default password for these networks is the router's MAC finished with the last digit 0, lowercase letters are often but sometimes can be capitalized. An example:
Code:
SSID: wifimedia_R-1234 MAC: 00: 26: 5B: 1E: 28: A5 The key will be: 00265b1e28a0 It can also be: 00265B1E28A0
As can be seen the safety of these routers is ridiculous, needless or capture packets or use the R-WlanXDecrypter program or anything.
R-wlanX networks with WEP:
The first is to clarify that neither the SSID or MAC provides details on the key. Normally the number of SSID channel usually (but not always) the AP. Not always the exact format of "R-wlanX" is true, sometimes mixed uppercase lowercase, no spaces sometimes, sometimes scripts, sometimes nothing separating the words; and sometimes additional words are in the SSID.
The most universal way to define default passwords R is being followed zeros numbers. How many numbers before the 0's? Typically 8, on occasion independent 6. Now we have four possibilities this type of default passwords (passwords ruling over 128 bits):
- Password WEP 128 bit ASCII (ex .: "2010945600000"): The most common password
- Password WEP 128 bit Hexadecimal (eg .: 20: 10: 94: 56: 00: 00: 00: 00: 00: 00: 00: 00: 00): Rare, but if any Haila
- 64 bit ASCII WEP Password: I've never seen one of this type
- Password WEP 64 bit hexadecimal (eg 20: 10: 94: 56: 00): They look quite
Do they mean something numbers? this topic is quite mysterious:
-Some Key start for one year (ex .: "2008") followed by four random numbers; is believed that the year is manufacturing router, but we found many future years (ex .: "2023"), so do not seem to be the case. Also most begin with 2 keys, if we reduce the search range can start looking for clues that start with 2. It was recently discovered that this number seems to be the ID that R assigned to your client (completely unknown thing for us that only is present in their bills).
-In Other cases, especially when treated 6 numbers followed by 0's (instead of 8) is believed to be the phone number without the prefix. Knowing this does not help us much but if these keys are only 6 numbers followed by 0's instead of 8, which reduces very sustencialmente our interval search
Well, whatever the origin of these numbers, we find that only vary at most 8 digits, which are always numbers, so we have 10 ^ 8 = 100,000,000 possibilities for each type of passwords, which are also not many. In an actual laptop midrange all the keys would be checked in 2 hours or less so.
R-wlanX networks with WPA keys:
Today it is more common to see routers with default keys R WPA with WEP keys, although the pattern is similar to WEP passwords. In this case the default passwords are key 8 digits but without following the 0's, the XXXXXXXX (ex .: "20109456") style. This number seems to be the ID of the client, and it seems that this number also starts in most cases (so far in all tested) for 2, so that passwords are we would reduce only those that begin with 2 (Style 2XXXXXXX).
Also there have been cases WPA key 10 digits, although still only 8 variables digits, but with two 0's below (although these are much less common). XXXXXXXX00 style (ex .: "2010945600"). As with the keys to 8 digits only found cases of passwords that began 2 to 2XXXXXXX00 style.
The third pattern WPA key is detected is a 16 digit password, but it really is a password of 8 variables digits repeated twice, at ABCDEFGHABCDEFGH style (ex .: "2015483920154839").
A modest rate of cracking of 1000key / sec, it would take about 28horas to check the complete dictionary of keys. If we test only the keys that begin with 2, it would take about 3 hours to check.
This concludes the analysis and proceed to explain the application.
R-WlanXDecrypter
The program currently supports Unix and Windows platforms. The basic options are needed to create dictionaries for WEP passwords, and additional options, which I will explain later, are a way to create custom dictionaries, and also serve for WPA keys.
The project is now available with source code on GitHub. One tag for each version release will be created, and major developments are made on the master:
https://github.com/millanzarreta/R-WlanXDecrypter

Basic Options
- -n <nbits>: Create ... Although it is also compatible for larger keys as 512bits I have never found one of R such dictionary for key 64bit, 128bit, etc. If no parameter is specified the program gets a key of 128 bits default
- -h <sep>: a dictionary is created in hexadecimal format, is not an alternative format to store keys, but a different dictionary to one created without this option -h. The parameter <sep> is the character (decimal) bytes separator expressed in hexadecimal format, if not specified the default is: which is the symbol most often used for this function and using aircrack-ng
Using only these options can create universal dictionaries for R passwords with WEP keys. If creais dictionary for aircrack-ng is important to remember that supports dictionaries larger than 2GB. By default, the program creates keys 8 digits followed by 0's (and thus also include the 6-digit). The notes of the new version of aircrack-ng comment that dictionaries should support larger than 2GB, but empirically checking it to me still not working.
'First we will create a dictionary for passwords ASCII 128bit, will occupy 1,40GB:
Code:
R-WlanXDecrypter rwlan128.txt
Now we will create a dictionary for passwords Hexadecimal 64-bit, take 1,48GB:
Code:
R-64 -n -h WlanXDecrypter rwlan64hex.txt
With these two dictionaries should suffice for most routers R. Even so can always generate a password dictionary to Hexadecimal 128bit. This dictionary occupy 3,72GB:
Code:
R-WlanXDecrypter rwlan128hex.txt -h
If we create the dictionary for aircrack-ng remember dictionaries that does not support more than 2GB, so we have to split into two this dictionary (for example, two dictionaries of 1,86GB each):
Code:
R-WlanXDecrypter rwlan128hex1.txt -h -max 49,999,999 R-WlanXDecrypter rwlan128hex2.txt -h -min 50000000
-Also Can create a dictionary for 64-bit ASCII key, but never see any of this in R dictionary occupies only 683KB:
Code:
R 64 -n-WlanXDecrypter rwlan64.txt
-
It is assumed that these dictionaries are all keys that can contain a
router R, but note that it can exist keys longer than 128 bits, although
I've never seen any so far.
- -c <nchar>: By default dictionary words vary 8 digits and then filled with 0's horn complete the key length. You can use this option if you want to specify a different number of variables digits
- -cm <decchar>: Default keys are padded with 0's. With this parameter we can specify another symbol (specify the decimal character code)
- -min <num>: With this option you can define the beginning of the dictionary specifying the minimum value. The specified minimum value excluding the filler (ie, counting only the number formed by the variable bytes)
- -max <num>: This option can define the end of the dictionary specifying the maximum value. The maximum value excluding filler (ie, counting only the number formed by the variable bytes) specified
- -Rep <num>: With this option you can specify that the variable part of the generated passwords are repeated num times
- -r: If you specify this option dictionary words are separated by LF byte (char 10). Default are separated by 2 bytes: CR + LF (char 13) (char 10). Most programs recognize both formats. With this option save 1 byte per word.
- -m <nbytes>: Do the same as -n (why does not support that option) but with this option can manually set the number of bytes of the key. When we talk about passwords 128bit say, 24 of these are used for IV, so the key is actually only (128-24) / 8 = 13-n bytes. 64 is equivalent to -m 5, -n 128 to 13 -m, etc ...
- q: Do not show the status of the process of creating the dictionary
With the default options dictionaries generated are of great size and with many words, and can take a long time depending on the equipment check them all. With these advanced options can be defined more custom dictionaries. Several useful examples:
As we said, sometimes the keys are only 6 numbers followed by 0's, then create the above dictionaries (except 64bit ASCII because it makes no sense to reduce it) but for 6 bytes variables instead of 8. The dictionaries created 67,7MB occupy only 3 together. In this way we can do a quick check with the aircrack-ng for key numbers with 6 variables before using large dictionaries:
[/ List]
Code:
R-WlanXDecrypter rwlan128-c6.txt -c 6
Code:
R-WlanXDecrypter rwlan64hex-c6.txt -h -n 64 -c 6
Code:
R-WlanXDecrypter rwlan128hex-c6.txt -h -c 6
-and Named many of the default passwords of R typically start -min and -max 2. Using dictionaries can define only that range (starting with 2). The 3 dictionaries that are creating (128bit ascii, hex 64bit and 128bit hex) occupy the tenth of each:
Code:
R-WlanXDecrypter rwlan128-start2.txt -min -max 20000000 29999999
Code:
R-WlanXDecrypter rwlan64hex-start2.txt -h -n 64 -min -max 20000000 29999999
Code:
R-WlanXDecrypter rwlan128hex-start2.txt -h -min -max 20000000 29999999
Case WPA:
We can use the program with options to create a dictionary views for key WPA. In this case we have to indicate that you create a dictionary of 8 digits, all variables. The dictionary will 100,000,000 keys and take 953.67MB:
Code:
R -m-WlanXDecrypter rwlanwpa.txt 8
If we want to reduce the search time, we can create a dictionary that contains only the keys starting with 2. The dictionary has 10,000,000 and occupies 95.37MB keys:
Code:
R-WlanXDecrypter rwlanwpa-start2.txt -m 8 -min -max 20000000 29999999
Most of R WPA keys are 8 figures, but also have detected some cases key 10 digit numbers with 8 variables followed by two 0's. To create the dictionary would be as follows:
-The Complete dictionary for WPA 10 has 100,000,000 key figures and occupies 1144.41MB:
Code:
R -m-WlanXDecrypter rwlanwpa10.txt 10
If you only want to reduce the search time, we can test the keys starting with 2. This dictionary has 10,000,000 and occupies 114.44MB key.
Code:
R-WlanXDecrypter rwlanwpa10-start2.txt -m 10 -min -max 20000000 29999999
Finally, it has also detected a pattern of 16-digit passwords that are actually passwords 8 variables digits that repeat.
-The Complete dictionary for WPA 16 has 100,000,000 key figures and occupies 1716.61MB:
Code:
R-WlanXDecrypter rep1.txt rwlanwpa16-1 -m 16 -Rep
If you only want to reduce the search time, we can test the keys starting with 2. This dictionary has 10,000,000 and occupies 171.77MB key.
Code:
R-WlanXDecrypter rwlanwpa16-rep1-start2.txt -m 16 -Rep 1 -min -max 20000000 29999999
So far all the networks analyzed starting with the number 2. Therefore it is recommended to start with dictionaries that only recojen keys starting with 2 and use the general dictionaries of 8 and 10 figures only in the event that they do not work.
Discharge
Includes compiled versions for linux and windows and source code.
Current-version (1.0):
-mirror 1: https://www.dropbox.com/s/5aojiwb58nqqvkm/R-WlanXDecrypter1.0.zip?dl=1
-mirror 2: https://github.com/millanzarreta/R-WlanXDecrypter/raw/release-1.0/R-WlanXDecrypter1.0.zip
Old-versions (0.9):
-mirror 1: https://www.dropbox.com/s/srlrovcubxm3son/R-WlanXDecrypter0.9.zip?dl=1
-mirror 2: https://github.com/millanzarreta/R-WlanXDecrypter/raw/release-0.9/R-WlanXDecrypter0.9.zip
Old-versions (0.8):
-mirror 1: https://www.dropbox.com/s/p0mt5t0uyjmqdxt/R-WlanXDecrypter0.8.rar?dl=1
-mirror 2: https://github.com/millanzarreta/R-WlanXDecrypter/raw/release-0.8/R-WlanXDecrypter0.8.rar
Changelog
v1.0 [27/10/2014]
-----------------
+ Added option -Rep <num> which allows the variable portion repeat <num> times
+ Change in type of variables with more acceptable
+ Fixed error showing the process of creating bad if the dictionary was larger than 2GB
+ Fixed a bug that was produced at times to create hexadecimal dictionaries and that produced a word size than the specified
+ Fix several minor bugs
v0.9 [11/10/2010]
-----------------
+ Show final file size and number of keys
Show status process +
+ Added -q quiet mode
+ Fixed bug in -min and -max options
+ Small loop optimization key generator
+ Correction of small general failures
v0.8 [06/10/2010]
-----------------
+ First public release
Appendix: Using dictionaries Hexadecimal in aircrack-ng
To define aircrack-ng one hexadeximal dictionary must specify h: before the path of the dictionary and we must always specify the length of the WEP keys in the dictionary are using:
Code:
aircrak-ng -n 128 -WH: "rwlan1281hex.txt" captura.cap
Code:
aircrak-ng -n 64 -WH: "rwlan64hex.txt" captura.cap
It seems that the new version of aircrack-ng these bugs still present.


0 comments for "R-WlanXDecrypter 1.0 For Windows"